Have you ever opened your inbox and found it flooded with unwanted emails offering questionable deals, miracle cures, or fake job offers? You’re not alone. These unsolicited messages are called spam, and they’re an everyday nuisance for people worldwide. But spam doesn’t just show up in your email; it can appear as text messages, comments on social media, or even search engine results. In this guide, we’ll explain what spam is, how to recognize its many forms, and the practical steps you can take to protect yourself.
If you’re warming a new domain, start with our 4-week email warm-up guide to avoid 40 % inbox placement.
What Is Spam?
Spam refers to unsolicited and irrelevant messages sent over the internet, usually to a large number of recipients. It most commonly appears in email inboxes but can also show up in text messages, social media platforms, and messaging apps. The goal of spam can vary: some messages are harmless advertisements, while others may contain dangerous links or attachments designed to steal personal information.
The term “spam” has been around for decades, originating as a reference to a 1970s Monty Python sketch where the word “spam” (referring to the canned meat product) is repeated excessively. The concept of something repetitive, intrusive, and unwanted was a perfect fit for what we now call digital spam.
Common Types of Spam to Watch Out For
As we mentioned, spam isn’t limited to one form. It can take many shapes depending on the medium and the scammer’s intent. Here are the most common types:
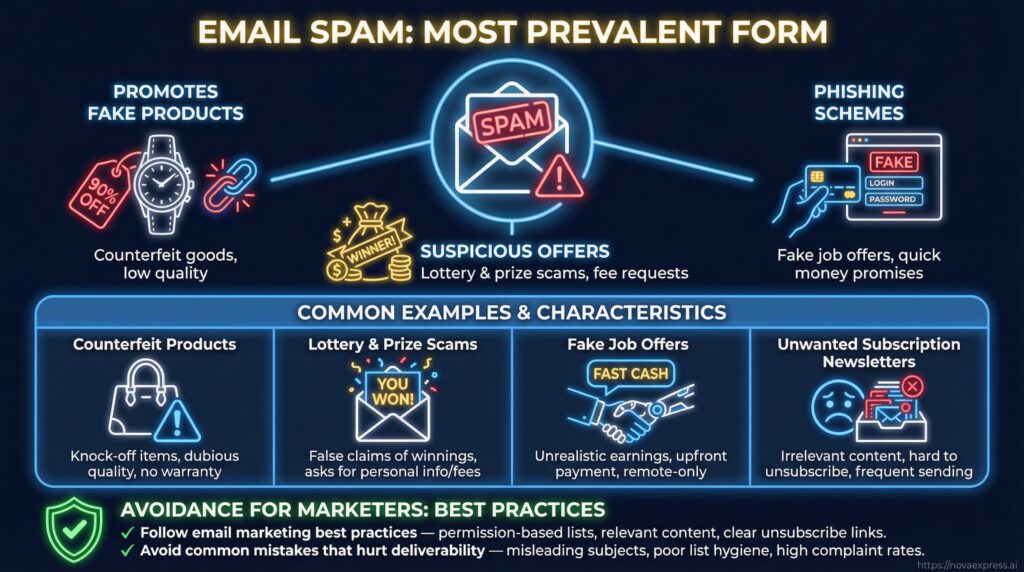
1. Email Spam
Email spam is the most prevalent form. These emails often promote fake products, suspicious offers, or phishing schemes. Some common examples include:
- Promotions for counterfeit products
- Lottery and prize scams
- Fake job offers promising quick money
- Unwanted subscription newsletters
To avoid being marked as spam, marketers should follow email marketing best practices and avoid common mistakes that hurt deliverability.
2. Text Message Spam
Text spam, also known as SMS spam, involves unsolicited messages sent to your phone. These often contain malicious links or offers designed to trick you into revealing sensitive information.
3. Social Media Spam
Spam on social media platforms usually comes in the form of fake accounts, irrelevant messages, and suspicious links in posts or comments. You might also encounter:
- Fake giveaways
- Phishing links in direct messages
- Scams impersonating well-known brands
4. Search Engine Spam
This type involves websites that manipulate search engine results to drive traffic to low-quality or malicious sites. For example, keyword-stuffed pages or misleading content can rank high in search results to trick users.
5. Comment Spam
If you’ve ever read blog posts or watched videos online, you’ve probably seen spam comments promoting shady products or services. These are often automated messages designed to spread links and advertisements.
How to Recognize Spam
Being able to spot spam is the first step to protecting yourself. While spam can be sneaky, there are a few telltale signs to look for, including:
- Unsolicited Content: If you didn’t sign up for it, it’s likely spam.
- Too-Good-To-Be-True Offers: Promises of free money, prizes, or instant results are major red flags.
- Poor Grammar and Spelling: Many spam messages contain obvious errors.
- Suspicious Links or Attachments: Avoid clicking on links or downloading attachments from unknown senders.
- Generic Greetings: Emails addressed to “Dear Customer” or similar phrases may indicate spam.
If you’re ever unsure, trust your instincts. It’s always better to delete a suspicious message than to risk interacting with it.
Similarly, when crafting your own email campaigns, writing compelling subject lines that get opened without looking spammy is crucial for success.
Spam vs Phishing: What’s the Difference?
Although spam and phishing often overlap, they are not the same. Here are the key differences:
- Spam: Spam refers to unsolicited messages, usually for advertising purposes. Not all spam is malicious; some are simply unwanted.
- Phishing: Phishing is a targeted form of spam designed to trick you into providing sensitive information, such as passwords, credit card details, or login credentials. Phishing emails often impersonate trusted companies or individuals to appear legitimate.
For example, an email claiming to be from your bank asking you to verify your account details by clicking a link is a phishing attempt. On the other hand, a generic advertisement for cheap medications is plain spam.
How Spammers Find You
So, how does spam land in your inbox or phone? Spammers use several methods to collect and target your information:
- Public Listings: Posting your email address or phone number on forums, websites, or social media makes it easy for spammers to find you.
- Data Breaches: Hackers leak user information from companies, which is then used for spam campaigns.
- Info Sold to Third Parties: Some businesses sell customer data to advertisers or marketers, which ends up being used for spam.
- Sign-Ups on Untrustworthy Sites: Entering your details on unreliable sites can lead to your information being sold or shared.
- Automated Guessing: Some spammers use software to randomly generate email addresses and phone numbers.
- Interacting with Spam: Opening spam emails or clicking links can confirm your contact information is active.
How to Protect Yourself from Spam
Protecting yourself from spam requires a combination of good habits and technology. Here are some practical steps you can take to reduce spam and avoid its risks:
1. Use a Spam Filter
Email providers usually offer built-in spam filters that automatically identify and move spam emails to a separate folder. Check your email settings to ensure this feature is active, and periodically review your spam folder to catch any legitimate emails that were mistakenly flagged.
If you’re sending marketing emails, understanding key email marketing metrics like open rates and deliverability helps you avoid spam filters.
2. Don’t Share Your Email Address Publicly
Posting your email address on websites, forums, or social media can expose it to spam bots that scan the web for targets. If you must share it, consider using a disposable or secondary email address to protect your primary inbox.
3. Be Cautious with Unsubscribing
While it’s tempting to unsubscribe from spam emails, clicking the unsubscribe link can backfire. Scammers often use these links to confirm that your email address is active. Only unsubscribe from emails sent by verified, legitimate sources.
Learn more about email unsubscribe best practices and why easy opt-outs improve deliverability.
4. Never Click Suspicious Links or Download Attachments
Suspicious emails may contain dangerous links or attachments that install malware on your device. Before clicking, hover over links and closely examine the URL. If anything looks unfamiliar or mismatched, delete the email immediately.
5. Use Strong Email Security Settings
Enhance your email security by enabling two-factor authentication (2FA). This adds a second layer of protection, requiring both your password and a verification code to access your email account.
For businesses sending marketing emails, understanding data privacy and security in email marketing is crucial to maintain trust and comply with regulations.
6. Report Spam
Most email services allow you to mark messages as spam. Reporting spam not only cleans up your inbox but also helps improve the platform’s spam detection tools, reducing spam for other users.
7. Keep Software Updated
Outdated software can have security vulnerabilities that spammers exploit. Regularly update your email apps, web browsers, and antivirus programs to ensure you’re protected against the latest threats.
Final Thoughts
Spam has been around for decades, and it’s unlikely to disappear anytime soon. However, with the right knowledge and tools, you can protect yourself and minimize its impact. By understanding what spam looks like, recognizing its risks, and adopting safe online practices, you can keep your inbox clean and your information secure. Remember, a little vigilance goes a long way, and when in doubt, it’s always best to ignore and delete.
Want to keep your email campaigns spam-free and secure? Start with Nova Express to create targeted, compliant emails that reach inboxes and drive engagement safely! Learn how to start your first email campaign or explore our 270+ free email templates to launch professional campaigns quickly.
❓ Frequently Asked Questions (FAQ)
What is spam and why is it a problem?
Spam is any unsolicited message sent in bulk over the internet — by email, text, social media, or comments. While some spam is just annoying advertising, other types can carry malware, phishing links, or scams. According to CISA, spam remains a major cybersecurity risk because it can lead to data theft and device compromise.
How can I tell if an email is spam?
Watch for these signs:
- You didn’t sign up for it
- Offers that seem too good to be true (e.g., “You won a prize!”)
- Poor grammar and spelling mistakes
- Generic greetings like “Dear Customer”
- Suspicious links or unexpected attachments
When in doubt, delete it — don’t click or reply.
What’s the difference between spam and phishing?
Spam is a broad term for unwanted bulk messages. Phishing is a dangerous type of spam designed to steal your personal information by pretending to be a trusted source (like your bank or Amazon). All phishing is spam, but not all spam is phishing.
Can spam infect my phone or computer?
Yes. Clicking a malicious link or downloading an attachment from a spam message can install malware on your device. This can lead to stolen passwords, locked files (ransomware), or hidden spying software. Always avoid interacting with suspicious messages.
How can I stop receiving spam emails?
Use these proven methods:
- Turn on your email provider’s spam filter
- Never post your main email address publicly online
- Avoid clicking “unsubscribe” in suspicious emails (it confirms your email is active)
- Report spam to help improve filters
- Use strong security settings like two-factor authentication
Businesses can avoid being marked as spam by using clean lists and trusted platforms, such as Nova Express, to send compliant, targeted emails.
Understanding the difference between contact-based and send-based pricing models can also help you choose the right email marketing platform.
Sources:
- https://www.avast.com/c-spam
- https://en.wikipedia.org/wiki/Spamming
- https://www.constantcontact.com/blog/types-of-spam
- https://www.cisa.gov/news-events/news/reducing-spam
Nova Express Resources
- What is Nova Express?
- How to Start Email Marketing
- How to Start Your First Email Campaign
- Amazon SES Integration Guide
- Mailgun Integration Guide
- Email Warm-Up Guide
- AI Tools for Marketers
- NotebookLM for Marketers
- Nano Banana Pro: The Complete Guide for Marketers 2026
Start building that story today
About the author
Serafima Osovitny is a marketing manager at Nova Express. Passionate about turning complex marketing tactics into simple, actionable guides, she shares insights about email marketing and e-commerce. Follow her on Twitter: @OSerafimaA.









Your article helped me a lot, is there any more related content? Thanks!
Clear, practical, and easy to understand. It explains what spam really is without fear-mongering and gives useful tips I can actually apply to protect my inbox.